Share this
The Crypto Virus Strikes Again with a New Strain Called CryptoWall
by Bridget.Giacinto on Jul 2, 2014 10:36:59 AM
It looks like this new strain of file-encrypting ransomware, called CryptoWall (and a variant, CryptoDefense), is picking up where CryptoLocker left off. On the heels of the botnet takedown, which stopped the spread of CryptoLocker (after infecting over 250,000 computers), the Center of Internet Security (CIS) has reported an increase in new CryptoWall malware infections, which are targeted at Windows systems running Windows 8, 7, XP, and Vista. Much like its predecessor, this malware takes over your system, restricting access to your files and folders until you pay a ransom.
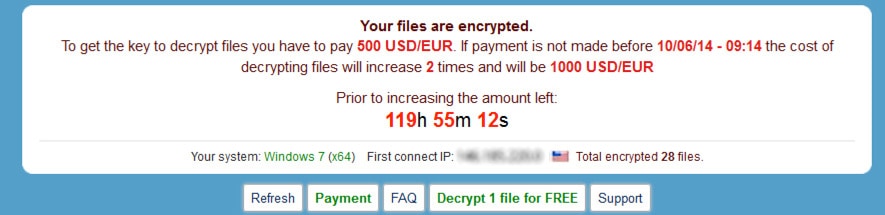
Unlike the $300 ransom of CryptoLocker, victims of CryptoWall are given a deadline to pay a $500 (or in some cases $600) ransom, or it doubles to $1,000. We’ve also seen the decryption price reportedly increase by 3 times. If victims don’t pay up before the new due date (shown with a countdown timer), victims lose their files for good. Once the key to decrypt their files is deleted, those files are rendered useless.
How CryptoWall Spreads
This strain of ransomware is distributed through a variety of sources, including phishing emails, fake application updates, and malicious ads on legitimate sites.
Phishing Email
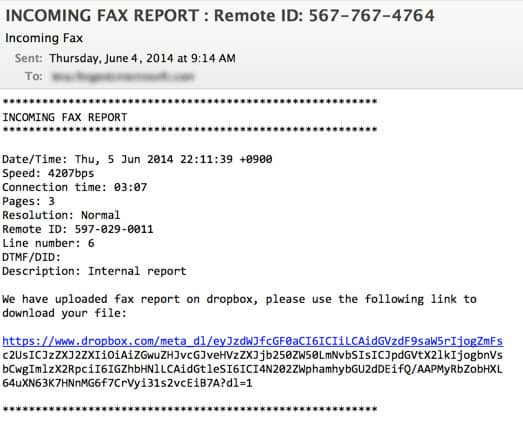
The virus is spread by getting users to click on a link within an email that is disguised as a fax or voicemail notification, or a UPS shipment tracking notice. These emails often include a Dropbox link, a link to a .zip file, or a shipment tracking link with varying subject lines such as “Incoming Fax Report…” or “Voice message from …” or “UPS Exception Notification,” for example. Be on the lookout for these types of emails and immediately delete them from your system. Don’t think that just because the link is to a Dropbox or from someone you know, that you are safe. Dropbox is a popular file-sharing software that many of us use (me included), but you need to be careful not to click on these links. It is known that cybercriminals are using Dropbox as their primary means of distributing the CryptoWall malware via email.
Malicious Advertisements
CryptoWall has been reported to use malicious ads on legitimate, well-known sites, such as Wiki.answers.com, apps.facebook.com, and eBay.in, altervista.com and theguardian.com to name a few. Because ad networks like to track where their clicks are coming from, Cisco has been able to pinpoint many high-profile sites that have inadvertently hosted malicious ads. These ads redirect unsuspecting users to malicious websites with the intent of infecting the user’s computer.
Once infected, an exploit kit called RIG (first reported by Kahu Security) is inserted onto the victim's computer. The kit checks for unpatched versions of Java, Flash, IE, or Silverlight multimedia. If systems are unpatched, the system is immediately exploited, and requests are made to download CryptoWall. It has been reported to take up to 24 hours for the CryptoWall virus to download and install onto your system once you have been infected, so you may have a small window of opportunity once infected.
How CryptoWall Works
CryptoWall malware encrypts your local files and demands you to pay a ransom to recover your files using a unique private decryption key housed on the cybercriminal’s servers. At the time of our research, there were no known tools or solutions to recover files encrypted with RSA-2048 encryption, without paying the ransom for the decryption key (stored on the CryptoWall Command-and-Control servers).
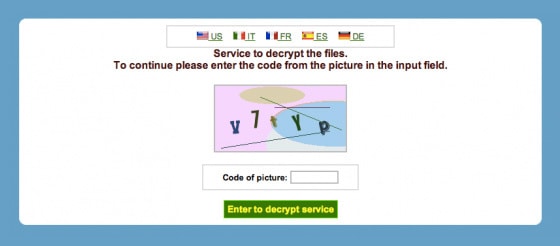
Once your files have been encrypted, you will receive a link to a TOR site (a browser that allows online anonymity). Cyber criminals use TOR sites to keep their identities hidden. You will be taken to a page that requires you to enter a CAPTCHA (where you are asked to type the letters of a distorted image) before presenting you with the ransom information.
The ransom amount can vary (we have seen $500-$600), but if not paid by a specified time, it will double or even triple.
Victims of CryptoWall are given the option to "Decrypt 1 file for FREE," which may be their way of showing you that they do have the ability to deliver on their so-called promise to decrypt your files.
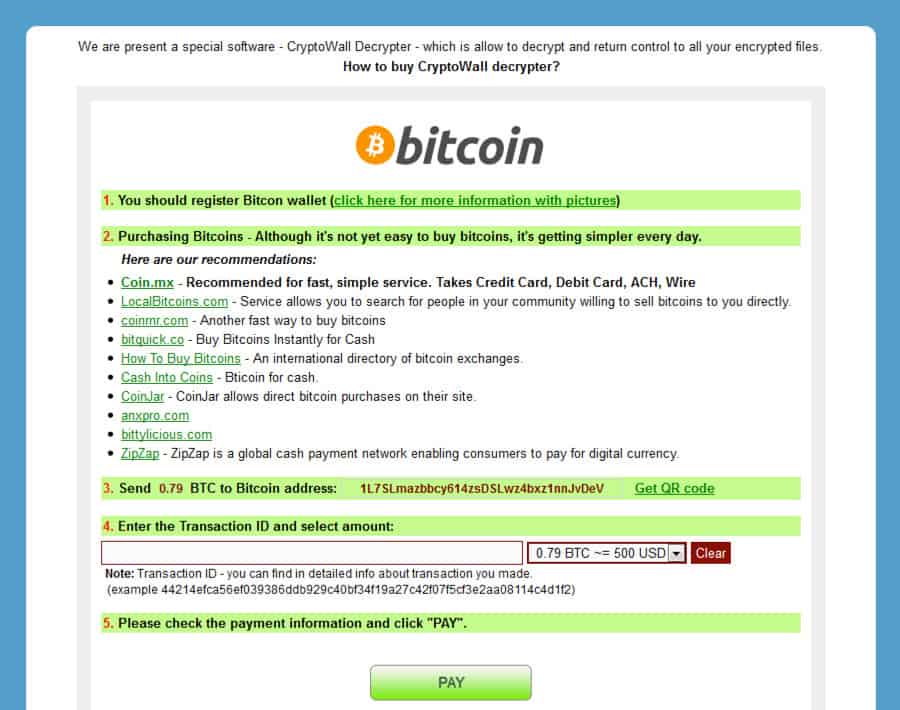
You are asked to purchase a special software called a CryptoWall Decrypter, using Bitcoin, which is supposed to allow you to decrypt your files.
If the ransom is not paid, you can kiss your files goodbye. That being said, paying the ransom does not guarantee the restoration of your files, and by paying them, you are in essence supporting cybercriminals. The fact that people are paying further cements their belief that this type of business model works. It’s just something to think about. In my humble opinion, it’s better to be proactive than reactive on this one.
Recommendations to Prevent CryptoWall Infection
1. Block Traffic from Known Fraudulent IP Addresses
It has been reported that there is a range of IP addresses that are owned and operated by criminal groups that contain a higher number of ransomware domains hosted on them. As a result, the Multi-State Sharing & Analysis Center (MS-ISAC) recommends the following:
Block traffic to/from IP address: 146.185.220.0/23 at your network perimeter.
2. Click with Care
Since we know that CryptoWall is spread through malicious ads, presented on well-known and reputable sites, be careful what you click on. Most advertisers are legitimate, but unfortunately, some users are abusing the system, using it as a means to lead users to malicious sites to hijack their files for ransom. For that reason, practice common sense and don’t click on ads you are uncertain about.
3. Use Anti-Virus and Anti-Malware Software
A word of advice, not all anti-virus software will protect you from malware. You may also need anti-malware software. Check with your provider to see if they are staying on top of the new strains of Crypto malware. Also, make sure your software definitions stay up to date, to ensure that you are protected against any new threats that pop up.
4. Keep Regular Backups of Your Data
The ideal situation is to be proactive here. Plan and keep regular backups of your data. That way, should you become a victim of CryptoWall, you can just remove the ransomware virus from your system and restore your files from your backup. NovaBACKUP offers an affordable PC backup software solution that will allow you to set up automatic backups of your files and create disaster recovery image backups.
5. Don’t Click on Suspicious Emails
If you receive any suspicious email, check the sender of the email to verify its legitimacy of the email, and don’t click on the link if you are uncertain. Specifically, stay away from emails that are disguised as faxes, voicemails, or even UPS (especially if you are not waiting for a shipment), as these are known sources for spreading CryptoWall malware.
6. Keep Patches Updated
Since it is a known fact that RIG exploit kits are targeting unpatched versions of Flash, Java, and Silverlight multimedia, by all means, keep these patches up to date.
Share this
- Pre-Sales Questions (91)
- Tips and Tricks (90)
- Best Practices (37)
- Industry News (37)
- Reseller / MSP (31)
- Security Threats / Ransomware (26)
- Disaster Recovery (24)
- Cloud Backup (22)
- Storage Technology (22)
- Compliance / HIPAA (20)
- Applications (18)
- Backup Videos (15)
- Virtual Environments (12)
- Technology Updates / Releases (7)
- Backup preparation (6)
- Infographics (5)
- Products (US) (4)
- Company (US) (1)
- Events (1)
- Events (US) (1)
- Unternehmen (1)
- February 2026 (1)
- January 2026 (2)
- December 2025 (2)
- November 2025 (1)
- October 2025 (2)
- September 2025 (1)
- August 2025 (1)
- July 2025 (1)
- June 2025 (2)
- May 2025 (2)
- April 2025 (2)
- March 2025 (1)
- February 2025 (2)
- January 2025 (2)
- December 2024 (1)
- November 2024 (2)
- October 2024 (1)
- September 2024 (2)
- August 2024 (1)
- July 2024 (2)
- June 2024 (3)
- May 2024 (1)
- April 2024 (2)
- March 2024 (3)
- February 2024 (2)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (1)
- July 2023 (1)
- May 2023 (1)
- March 2023 (3)
- February 2023 (2)
- January 2023 (1)
- December 2022 (1)
- November 2022 (2)
- October 2022 (2)
- September 2022 (1)
- July 2022 (1)
- June 2022 (1)
- April 2022 (1)
- March 2022 (2)
- February 2022 (1)
- January 2022 (1)
- December 2021 (1)
- September 2021 (1)
- August 2021 (1)
- July 2021 (1)
- June 2021 (1)
- May 2021 (2)
- April 2021 (1)
- March 2021 (1)
- February 2021 (1)
- January 2021 (1)
- December 2020 (1)
- November 2020 (1)
- October 2020 (1)
- September 2020 (3)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (1)
- March 2020 (2)
- February 2020 (2)
- January 2020 (2)
- December 2019 (1)
- November 2019 (1)
- October 2019 (1)
- August 2019 (1)
- July 2019 (1)
- June 2019 (1)
- April 2019 (1)
- January 2019 (1)
- September 2018 (1)
- August 2018 (3)
- July 2018 (2)
- June 2018 (2)
- April 2018 (2)
- March 2018 (1)
- February 2018 (1)
- January 2018 (2)
- December 2017 (1)
- September 2017 (1)
- May 2017 (2)
- April 2017 (4)
- March 2017 (4)
- February 2017 (1)
- January 2017 (1)
- December 2016 (1)
- October 2016 (2)
- August 2016 (3)
- July 2016 (1)
- June 2016 (2)
- May 2016 (6)
- April 2016 (5)
- February 2016 (1)
- January 2016 (7)
- December 2015 (6)
- November 2015 (2)
- October 2015 (5)
- September 2015 (1)
- July 2015 (1)
- June 2015 (2)
- May 2015 (1)
- April 2015 (3)
- March 2015 (3)
- February 2015 (3)
- October 2014 (2)
- September 2014 (6)
- August 2014 (4)
- July 2014 (4)
- June 2014 (3)
- May 2014 (2)
- April 2014 (3)
- March 2014 (4)
- February 2014 (5)
- January 2014 (5)
- December 2013 (4)
- October 2013 (6)
- September 2013 (1)