Share this
How Ransomware Has Changed the Way We Think About Backup
by Nathan.Fouarge on Apr 17, 2024 11:57:52 AM

Backup used to be a way to get your data back when a hard drive failed or a system outlived its purpose. That is, in most cases, you could restore data from a backup made a day or two earlier with little or no data loss. This led to backup strategies that, for example, set retention to cover short-term data loss.
The Threat of Ransomware
Until a few years ago, when ransomware unfortunately became part of our everyday lives. In recent months, it has received even more press due to the growing popularity of Generative AI, which is used by cybercriminals and other bad actors to increase the volume of their attacks without much effort. And these attacks are a growing threat to small and medium-sized businesses, managed service providers, and other "non-enterprises”.
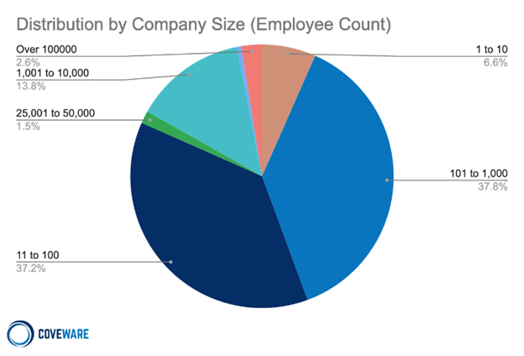
A report from Coveware found out that 82% of attacks that took place in 2021 impacted organizations with less than one thousand employees. Source: tech.co.
So Why Is Ransomware So Dangerous?
Most of an organization's information is stored in digital form and resides on multiple hard drives and cloud storage. Ransomware encrypts every Bit (pun intended) it can reach, including network files and connected devices, rendering an organization's information useless.
As of 2023, over 72 percent of businesses worldwide were affected by ransomware attacks.
Source: Statista
This means that if those files and data are inaccessible due to ransomware encryption, a company can't fulfill orders and support its customers, resulting in lost revenue. And if a company can't generate revenue, it's only a matter of time before they have to go out of business. Even if they can manage to keep the doors open, damage to a business's reputation, legal ramifications, or lost information are still valid concerns.
Enhancing Your Backup Strategy
Unlike a failed hard drive, ransomware sneaks into the system and gets comfortable for weeks before attacking. This means that a backup from yesterday might initially help you recover your data after a ransomware attack. But it will likely lead to another attack shortly after the first one is resolved.
That's not to say that backups are useless. To be clear, they are not effective in preventing ransomware attacks (that's what security software is for). Backups are rather a last resort in the worst-case scenario.
It took 31% of organizations between one and six months to recover from a ransomware attack after paying the ransom. Meanwhile, 45% of those using backups recovered within a week.
Source: Sophos 2023 Ransomware Report
That's why it's critical to recognize the importance of a backup strategy that takes into account the nature of ransomware, while not ignoring the still very common causes of data loss, such as human error, hardware failure, stolen devices, and natural disasters. It is more about taking a different approach to recoverability. If a hard drive fails or a laptop is stolen, you can take yesterday's backup and restore it. To effectively restore after a ransomware attack, different considerations apply.
Make sure you have multiple copies of your data in multiple locations to ensure redundancy, meaning you can recover from one copy of your data even if the other is inaccessible. At least one of these backup locations should be somewhere beyond the reach of ransomware. It is essential to have a separate storage environment dedicated solely to backups, ideally not connected to the production environment. However, having multiple copies of your data is not enough. Make sure each copy consists of multiple versions of your data from different time periods, such as a day, week, or month ago.
Encrypting backups in transit and at rest prevents ransomware from accessing the data in your backup files. While ransomware can still encrypt the already encrypted backup files themselves, it can't access and read any of your backup data.
30% of ransomware attacks where data was encrypted reported that data was also stolen.
Source: Sophos 2023 Ransomware Report
The Benefits of Using Cloud Storage for Your Backups
 As mentioned above, one of your backups should be stored on media far from your office, ideally in another city (with NovaBACKUP and our own cloud storage, you can keep your backups separate from your production environment, adding an extra layer of security to your data protection strategy). By using the cloud as one of your backup destinations, you avoid the risk of you or your customers forgetting their backups in the office (which happens far too often). After all, what good is an offsite backup if it is not really offsite?
As mentioned above, one of your backups should be stored on media far from your office, ideally in another city (with NovaBACKUP and our own cloud storage, you can keep your backups separate from your production environment, adding an extra layer of security to your data protection strategy). By using the cloud as one of your backup destinations, you avoid the risk of you or your customers forgetting their backups in the office (which happens far too often). After all, what good is an offsite backup if it is not really offsite?
It also ensures that the data is actually stored on the offsite media without the risk of human error. We've seen companies swap out their drives every night without checking to see if the backup was even running. Automatic backups to a storage device you can control from anywhere can be scheduled hourly, daily, or weekly for consistent data protection.
Plus, the cloud ensures you can access your data from anywhere. There is no need for a trip to the vault or a search through hundreds of tapes.
Read more about how you can leverage cloud backup for maximum data protection in our ebook here.
Preparing for Data Recovery
No one wants to be hit by a ransomware attack, but there is no way to prevent it from happening 100% of the time. So be prepared and test your backups frequently!
Regular testing helps identify potential problems or gaps in the recovery process, so you can proactively make adjustments. Another benefit is that you will know how a restore works, reducing stress and wasted time trying to figure out what to do. Work with your backup vendor during your restore tests to learn all the best practices and the easiest ways to do it. And don't forget to document your recovery scenarios.
 Of course, we are only scratching the surface here. If you’d like to dig deeper into setting up a comprehensive backup strategy, take a look at our ultimate small business guide to protecting business-critical data.
Of course, we are only scratching the surface here. If you’d like to dig deeper into setting up a comprehensive backup strategy, take a look at our ultimate small business guide to protecting business-critical data.
And if you have any further questions, feel free to request a call here.
Share this
- Pre-Sales Questions (112)
- Tips and Tricks (95)
- Industry News (60)
- Reseller / MSP (37)
- Security Threats / Ransomware (30)
- Applications (28)
- Best Practices (27)
- Cloud Backup (25)
- Disaster Recovery (25)
- Backup Videos (24)
- Compliance / HIPAA (23)
- Storage Technology (21)
- Virtual Environments (17)
- Technology Updates / Releases (9)
- Infographics (8)
- Backup preparation (3)
- Company (US) (1)
- Events (1)
- Events (US) (1)
- Products (US) (1)
- April 2024 (1)
- March 2024 (2)
- February 2024 (2)
- January 2024 (1)
- December 2023 (1)
- November 2023 (1)
- October 2023 (1)
- September 2023 (1)
- August 2023 (1)
- July 2023 (1)
- May 2023 (1)
- March 2023 (3)
- February 2023 (2)
- January 2023 (3)
- December 2022 (1)
- November 2022 (2)
- October 2022 (2)
- September 2022 (2)
- August 2022 (2)
- July 2022 (1)
- June 2022 (1)
- April 2022 (1)
- March 2022 (2)
- February 2022 (1)
- January 2022 (1)
- December 2021 (1)
- November 2021 (1)
- September 2021 (1)
- August 2021 (1)
- July 2021 (1)
- June 2021 (2)
- May 2021 (2)
- April 2021 (1)
- March 2021 (2)
- February 2021 (1)
- January 2021 (2)
- December 2020 (1)
- November 2020 (1)
- October 2020 (2)
- September 2020 (4)
- August 2020 (2)
- July 2020 (1)
- June 2020 (1)
- May 2020 (1)
- April 2020 (1)
- March 2020 (3)
- February 2020 (2)
- January 2020 (2)
- December 2019 (1)
- November 2019 (1)
- October 2019 (1)
- August 2019 (1)
- July 2019 (1)
- June 2019 (1)
- April 2019 (1)
- February 2019 (1)
- January 2019 (1)
- December 2018 (1)
- November 2018 (2)
- August 2018 (3)
- July 2018 (4)
- June 2018 (2)
- April 2018 (2)
- March 2018 (2)
- February 2018 (2)
- January 2018 (3)
- December 2017 (1)
- September 2017 (1)
- May 2017 (2)
- April 2017 (5)
- March 2017 (4)
- February 2017 (1)
- January 2017 (1)
- December 2016 (1)
- November 2016 (1)
- October 2016 (2)
- September 2016 (1)
- August 2016 (3)
- July 2016 (2)
- June 2016 (3)
- May 2016 (7)
- April 2016 (8)
- March 2016 (1)
- February 2016 (3)
- January 2016 (12)
- December 2015 (7)
- November 2015 (5)
- October 2015 (6)
- September 2015 (2)
- August 2015 (4)
- July 2015 (2)
- June 2015 (2)
- May 2015 (1)
- April 2015 (5)
- March 2015 (3)
- February 2015 (4)
- January 2015 (2)
- October 2014 (5)
- September 2014 (8)
- August 2014 (5)
- July 2014 (8)
- June 2014 (5)
- May 2014 (5)
- April 2014 (9)
- March 2014 (7)
- February 2014 (7)
- January 2014 (5)
- December 2013 (5)
- October 2013 (7)
- September 2013 (2)

